AWS History and Timeline regarding Amazon Cognito - Overview, Functions, Features, Summary of Updates, and Introduction
First Published:
Last Updated:
This time, I have created a historical timeline for Amazon Cognito, a serverless and fully managed authentication and authorization service that was announced and became Generally Available (GA) on July 10, 2014.
Today, July 10, 2024, marks the 10th anniversary of the day Amazon Cognito was announced and became generally available (GA).
To commemorate this significant milestone, I have written this article as a celebration.
Just like before, I am summarizing the main features while following the birth of Amazon Cognito and tracking its feature additions and updates as a Current Overview, Functions, Features of Amazon Cognito.
I hope these will provide clues as to what has remained the same and what has changed, in addition to the features and concepts of each AWS service.
Background and Method of Creating Amazon Cognito Historical Timeline
The reason for creating a historical timeline of Amazon Cognito this time is none other than that Amazon Cognito will celebrate its 10th anniversary since the announcement in 2024.Another reason is that since Amazon Cognito was announced in July 2014, it has expanded its features to support various authentication methods, enhanced security measures, and improved integration with other AWS services and third-party providers. Therefore, I wanted to organize the information of Amazon Cognito with the following approaches.
- Tracking the history of Amazon Cognito and organizing the transition of updates
- Summarizing the feature list and characteristics of Amazon Cognito
There may be slight variations in the dates on the timeline due to differences in the timing of announcements or article postings in the references used.
The content posted is limited to major features related to the current Amazon Cognito and necessary for the feature list and overview description.
In other words, please note that the items on this timeline are not all updates to Amazon Cognito features, but are representative updates that I have picked out.
Amazon Cognito Historical Timeline (Updates from July 10, 2014)
Now, here is a timeline related to the functions of Amazon Cognito. As of the time of writing this article, Amazon Cognito has just reached its 10th anniversary, marking a decade of providing identity management solutions since its launch in July 2014.* The table can be sorted by clicking on the column names.
| Date | Summary |
|---|---|
| 2014-07-10 | Amazon Cognito is announced and becomes Generally Available (GA). Early Amazon Cognito offered Identity Pools functionality, which integrated with existing identity providers such as Amazon, Facebook, and Google, supported unauthenticated guest users, and securely managed user-specific data. It also provided Cognito Sync functionality, which handled data synchronization, allowing users to sync app settings and game states across devices. |
| 2014-09-29 | Developer authenticated identities are added, allowing the use of custom user ID systems. Users can now treat their own authentication and ID management systems as identity providers for Amazon Cognito. |
| 2014-10-23 | Support for OpenID Connect providers is added. |
| 2014-11-06 | Support for push synchronization with Amazon Cognito Sync is added. |
| 2015-03-04 | Amazon Cognito Streams is added, enabling automatic streaming of user ID data to Amazon Kinesis, allowing control and insight into data streams. |
| 2015-04-09 | Integration with Amazon Cognito is added, allowing Amazon Cognito functions to be executed in response to important events in Amazon Cognito. |
| 2015-04-30 | Twitter and Digits are added as public login providers. |
| 2016-02-18 | AWS CloudTrail can now track the creation, modification, and deletion of Amazon Cognito Identity Pools and Amazon Cognito Sync. |
| 2016-04-19 | User sign-up and sign-in functionality can now be added to Amazon Cognito Identity Pools. |
| 2016-06-23 | Support for authentication using identity providers with SAML 2.0 is added. |
| 2016-07-28 | Amazon Cognito User Pools becomes Generally Available. Users can now create and maintain user directories, and add sign-up and sign-in functionality to mobile apps and web applications using User Pools. |
| 2016-09-01 | Bulk import functionality is added to Amazon Cognito User Pools. User migration from existing identity providers to Amazon Cognito User Pools becomes possible. AWS CloudTrail can now track the creation, modification, and deletion of Amazon Cognito User Pools. |
| 2016-10-06 | The ability for administrators to create user accounts is added to the Amazon Cognito console and API. |
| 2016-11-09 | When using the email and password option in AWS Mobile Hub, a fully managed user directory for the app can be provisioned in Amazon Cognito. |
| 2016-12-15 | Group functionality is added to Amazon Cognito User Pools. Role-Based Access Control (RBAC) is added to Amazon Cognito Identity Pools. |
| 2017-04-28 | Amazon Cognito is supported in AWS CloudFormation. |
| 2017-07-06 | Amazon Cognito achieves HIPAA eligibility and PCI compliance. Users can now use phone numbers or email addresses as usernames. |
| 2017-08-10 | Federation and built-in app UI features are added to Amazon Cognito User Pools. Users can now sign in to User Pools using OAuth 2.0 with Facebook, Google, Login with Amazon, and SAML identity providers. |
| 2017-09-26 | Integration with Amazon Pinpoint is added. Amazon Pinpoint can now be used for analytics of Amazon Cognito User Pools apps, and user data can be enhanced for Amazon Pinpoint campaigns. |
| 2017-11-28 | Amazon Cognito Advanced Security (Beta) is added. New security features are introduced to protect apps and users from malicious bots, protect user accounts from compromised credentials elsewhere on the internet, and automatically adjust sign-in challenges based on the calculated risk of sign-in attempts. |
| 2018-02-08 | Amazon Cognito Lambda Migration Trigger is supported. User existence can now be verified in User Pools, and user profile data can be copied from existing application directories to User Pools. |
| 2018-05-17 | Sign-in using OpenID Connect (OIDC) identity providers (such as Salesforce, Ping Identity) is added to Amazon Cognito User Pools. |
| 2018-06-04 | Custom domains can now be used for the hosted login UI in Amazon Cognito User Pools. |
| 2018-06-14 | Amazon Cognito Advanced Security becomes Generally Available. New security features are introduced to protect apps and users from malicious bots, protect user accounts from compromised credentials elsewhere on the internet, and automatically adjust sign-in challenges based on the calculated risk of sign-in attempts. |
| 2019-01-22 | Amazon Cognito announces a 99.9% Service Level Agreement (SLA). |
| 2019-03-26 | Tagging support is added. Information about tagging Amazon Cognito resources is added. |
| 2019-04-08 | Amazon SES email configuration feature is added to Amazon Cognito User Pools. User Pools can now be configured to use Amazon SES settings for Amazon Cognito to send emails to users. |
| 2019-05-06 | User password reset API is added, allowing administrators to set temporary or permanent passwords for end users. This becomes available to end users even when verified phone or email is not available. |
| 2019-10-07 | AWS CloudFormation adds support for securely and automatically configuring Amazon Cognito's hosted UI domain, configuring hosted UI customization, configuring IdentityProvider, configuring Amazon Cognito Advanced Security behavior, and configuring resource servers. |
| 2019-11-20 | Amazon Cognito User Pools supports Sign in with Apple. |
| 2019-11-26 | Amazon Cognito User Pools supports prioritizing password recovery methods for forgotten passwords. |
| 2020-01-10 | Amazon Cognito supports Amazon CloudWatch Usage Metrics. |
| 2020-02-05 | AWS CloudTrail supports logging of all API calls for Amazon Cognito User Pools. |
| 2020-02-12 | Amazon Cognito User Pools supports case-insensitive user aliases. It is now recommended to disable case sensitivity for usernames before creating a User Pool. |
| 2020-04-07 | Amazon Cognito Identity Pools supports Sign in with Apple. |
| 2020-08-12 | Amazon Cognito User Pools support customization of access token and refresh token expiration. |
| 2020-10-30 | Quota management and usage tracking for Amazon Cognito User Pools can now be done using AWS Service Quotas and Amazon CloudWatch metrics. |
| 2021-01-14 | Amazon Cognito Identity Pools can now simplify permission management for AWS resources through access control using identity provider user attributes. |
| 2021-06-02 | Amazon Cognito supports Amazon SNS SMS Sandbox. |
| 2021-06-10 | Amazon Cognito supports targeted sign-out by revoking refresh tokens in real-time. RevokeToken API and revocation endpoint are added, allowing users' refresh tokens to be revoked using the RevokeToken operation. |
| 2021-11-18 | A new console experience is added for Amazon Cognito User Pools. |
| 2022-03-14 | Amazon Cognito User Pools support same-region integration with Amazon SNS and Amazon SES. Amazon SNS can now be used for SMS messages and Amazon SES for email messages. |
| 2022-05-31 | Amazon Cognito Advanced Security's risk assessment is improved, allowing IP addresses to be propagated as part of the caller's context data in unauthenticated calls to Amazon Cognito. |
| 2022-08-11 | AWS WAF Web ACLs can now be associated with Amazon Cognito User Pools. |
| 2022-09-09 | Time-Based-One-Time-Password (TOTP) MFA devices can now be registered in Amazon Cognito's hosted UI. |
| 2022-10-24 | Deletion protection for Amazon Cognito User Pools is introduced. |
| 2023-02-15 | AWS CloudTrail can now record data events for Amazon Cognito Identity Pools. |
| 2023-05-16 | The console experience for Amazon Cognito Identity Pools is improved. |
| 2023-08-01 | Amazon Verified Permissions becomes Generally Available (GA), enabling an integrated authentication and authorization solution for applications that can validate policies based on Amazon Cognito attributes and authorize requests using Amazon Cognito tokens. |
| 2023-12-12 | Amazon Cognito Identity Pools support customization of access token content. Claims and scopes in User Pool access tokens can now be added, modified, and deleted. |
| 2023-12-19 | Amazon Cognito User Pools can now manage quotas for commonly used operations for identity creation and retrieval, and Identity Pool tag management through AWS Service Quotas. |
| 2024-02-01 | Amazon Cognito now allows sending signed SAML authentication requests, requesting encrypted responses from SAML ID providers, and using identity provider-initiated single sign-on (SSO) for SAML federation. |
| 2024-04-05 | Using Amazon Verified Permissions, only users in authorized Amazon Cognito groups can now access application APIs. |
| 2024-05-21 | When authenticating using Cognito tokens with Amazon Verified Permissions, Cedar policies can now be created based on Cognito group memberships. |
| 2024-05-30 | Amazon Cognito User Pools expand access token customization to support complex custom attributes such as arrays, maps, and JSON objects in both ID tokens and access tokens. |
Current Overview, Functions, Features of Amazon Cognito
From here, we will explain in detail the main features of the current Amazon Cognito.Amazon Cognito is a fully managed authentication service that allows mobile and web application developers to easily implement user authentication and data synchronization.
Amazon Cognito primarily offers two features.
The first, "User Pools," manages user directories, performs user authentication such as sign-up and sign-in, and can easily integrate the authentication framework required for applications. It also issues JWT tokens after authentication, which can be used for authorization within the application.
The second, "Identity Pools," enables authorization in the AWS environment by granting temporary AWS credentials to authenticated and unauthenticated users, allowing access to AWS resources.
Authentication primarily uses "User Pools" to verify the user's identity. For authorization, tokens issued by "User Pools" are used within the application, while access to AWS resources is controlled through "Identity Pools".
By using both of these, application developers can effectively manage user authentication information and access permissions.
Furthermore, Amazon Cognito can be easily integrated with other AWS services and supports synchronization of user data across devices, contributing to improved user experience.
When combined with access control using AWS IAM, it allows for secure operation of applications while maintaining development flexibility and enhancing security.
Use Cases for Amazon Cognito
Amazon Cognito is designed to simplify the handling of user information for application developers by securely managing authentication and authorization.The main use cases utilizing User Pools and Identity Pools, the key components of Amazon Cognito, include the following:
- User Authentication
Using User Pools to securely provide user registration and login functionality in mobile and web applications.
It also supports federated authentication through social ID providers (Facebook, Google, Amazon, Apple) as well as OIDC and SAML. - User Authorization and Resource Access Management
Using Identity Pools to grant temporary access to AWS resources for both authenticated and unauthenticated users.
Using the group feature of User Pools to manage permissions within the application. - Access Control to Server-Side Resources
Using tokens issued by User Pools to control access to server-side resources. - Resource Access via API Gateway and Lambda
Validating User Pools tokens in API Gateway to control access to Lambda functions or custom APIs. - Access to AWS Services
Combining User Pools and Identity Pools to grant temporary access rights to AWS services for authenticated users. - Third-Party Authentication and AWS Service Access
Using Identity Pools to allow users authenticated by third-party ID providers to access AWS services. - Access to AWS AppSync Resources
Using User Pools tokens to control access to AWS AppSync resources.
Using IAM credentials obtained from Identity Pools to send requests to AWS AppSync GraphQL APIs. - Synchronization of User Data Across Applications
Utilizing User Pools features to synchronize settings and application states across user devices.
Specific Use Case Examples
- Social Media Integrated Login
Providing functionality for users to log in using social accounts like Facebook or Google in web or mobile applications. User Pools handle this authentication. - Custom Authentication Flow for Mobile Apps
Implementing security-enhanced login processes using one-time passwords (OTP) or biometrics in mobile applications. User Pools support these authentication methods.
- Authorization for Serverless Backend Access
When applications access AWS services like Amazon S3 or DynamoDB, using Identity Pools to issue temporary AWS credentials, ensuring that only authenticated users can access resources. - Authentication in Microservices Architecture
In microservices architecture using API Gateway and Lambda, controlling access to each service using User Pools tokens. - User Group-Based Access Control
Using the group feature of User Pools to create user groups with different permission levels (e.g., administrators, general users) within the application and granting appropriate access rights to each. - Consistency of User Experience Across Cross-Platform Applications
Using User Pools to synchronize user profiles and authentication states across different platforms such as web, iOS, and Android, providing a consistent user experience. - GraphQL-Based Application Development
Combining User Pools and Identity Pools to control data access in GraphQL-based applications using AWS AppSync.
Conceptual Diagram of Amazon Cognito
From here, I will explain the main features and characteristics of Amazon Cognito, but before that, to make it easier to imagine the overall picture of Amazon Cognito, I will show a conceptual diagram of Amazon Cognito next.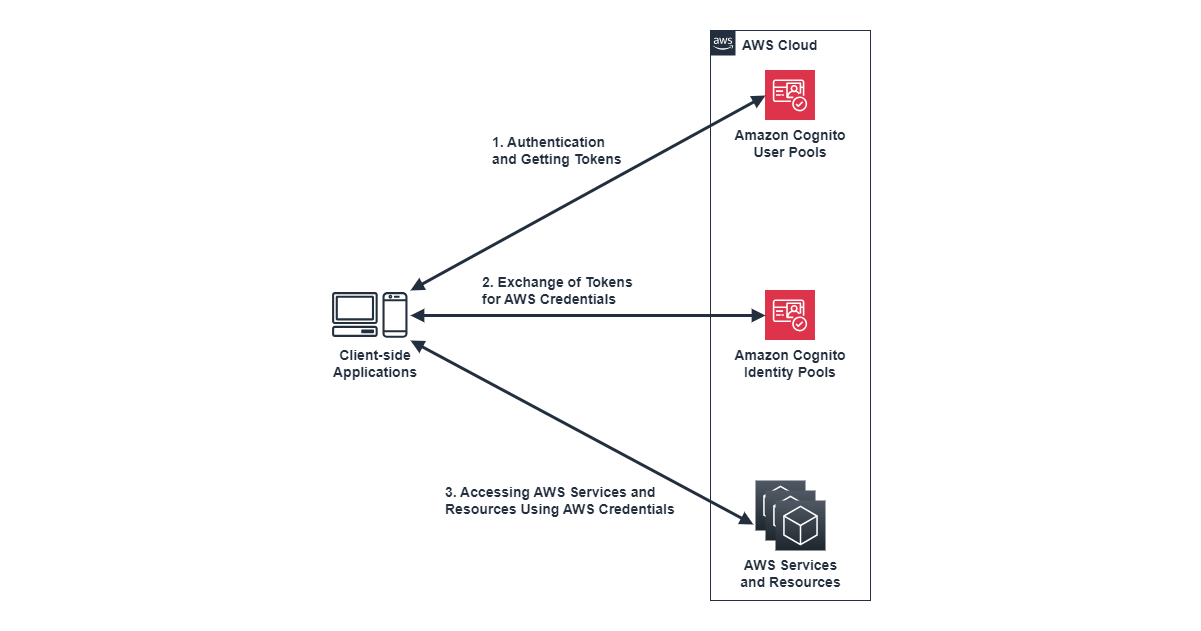
This conceptual diagram shows a typical authentication flow using User Pools and Identity Pools, the main features of Amazon Cognito.
The authentication process consists of the following three main steps:
- Users first authenticate with Amazon Cognito User Pools to obtain tokens.
- Next, these tokens are exchanged with Amazon Cognito Identity Pools for temporary AWS credentials.
- Finally, using these credentials, the application can access various AWS services and resources.
In the following sections, I will mainly explain the overview of the features of Amazon Cognito User Pools and Amazon Cognito Identity Pools.
Amazon Cognito User Pools
Overview of Amazon Cognito User Pools Features
Amazon Cognito User Pools is a comprehensive service for managing user authentication in web and mobile applications.It functions as a custom user directory and supports self-registration, administrator-led user creation, management, and authentication.
Operating based on the OpenID Connect (OIDC) standard, it issues JSON Web Tokens (JWTs), which are compact and self-contained signed JSON objects used for secure information transmission, providing direct authentication to applications and APIs.
One of the notable features of User Pools is its advanced integration with third-party Identity Providers (IdPs).
It supports integration with enterprise workforce identifiers, customer identifiers, and common social ID providers like Facebook, Google, Amazon, and Apple through SAML 2.0, OIDC, and OAuth 2.0 protocols.
In this integration, the attribute mapping feature plays a crucial role.
Users can flexibly map user attributes from external IdPs to attributes within the User Pool, ensuring data consistency and compatibility.
Furthermore, User Pools provide the ability to link federated users to existing user profiles.
This feature allows users to associate multiple authentication methods (e.g., local account and Facebook account) with the same user profile, enabling a seamless user experience.
On the security front, it offers advanced features such as multi-factor authentication (MFA), custom authentication flows, and protection against malicious activities.
User experience customization is also possible, allowing customization of the authentication process using Lambda functions and customization of the hosted UI design.
Monitoring and analytics capabilities are also robust, with integration with AWS CloudTrail, Amazon CloudWatch, and Amazon Pinpoint enabling detailed analysis and monitoring of user activities.
Additionally, integration with Amazon Cognito Identity Pools facilitates the management of access permissions to AWS services.
Combining these features, Amazon Cognito User Pools becomes an indispensable tool for modern application development, offering flexibility to handle complex authentication scenarios along with powerful security features.
The attribute mapping and user profile linking features make it easy to integrate and manage user information across different identity providers, enabling the provision of a seamless user experience.
Sign-in Methods for Amazon Cognito User Pools
Amazon Cognito User Pools provides flexible and powerful solutions for authentication and authorization in web and mobile applications.There are multiple ways users can access your application, which can be chosen based on your needs and existing infrastructure.
Below, we explain the main sign-in methods available in Amazon Cognito User Pools.
Direct Sign-in via User Pool
Amazon Cognito User Pools supports direct sign-in when functioning as a standalone user directory and identity provider (IdP).Users can sign in using Amazon Cognito's hosted UI or through a custom UI via the Amazon Cognito User Pools API.
Federation via Social IdP
Amazon Cognito User Pools supports OAuth 2.0 social sign-in.Users can sign in through social identity providers such as Google, Facebook, Amazon, and Apple.
Federation via Social IdP enables sign-in for consumer users while simultaneously importing their profile information into Amazon Cognito User Pools.
The imported information includes basic profile attributes of the user (e.g., name, email address, profile image URL).
These attributes are stored in the user profile within User Pools based on the configured mapping rules.
Federation via SAML IdP
Amazon Cognito User Pools also allows the use of SAML (Security Assertion Markup Language) federation.Amazon Cognito User Pools can be configured to accept requests from any SAML IdP.
Federation via SAML IdP is also suitable for sign-in and import using organizational user data, facilitating integration with existing organizational ID systems.
Through SAML authentication, user information such as attributes and roles can be securely transferred to Amazon Cognito User Pools and utilized for authentication in applications.
Federation via OIDC IdP
Amazon Cognito User Pools also enables federation through IdPs using the OpenID Connect (OIDC) protocol.Amazon Cognito can handle requests from any IdP compliant with OIDC.
Federation via OIDC IdP allows integration with various standards-compliant identity providers.
By combining these methods, you can provide flexible authentication options to users and seamlessly integrate with existing ID infrastructure.
Hosted UI
The Hosted UI of Amazon Cognito User Pools is a ready-to-use web interface for user authentication.It functions as an OAuth 2.0 compliant authorization server and has the following features:
- Provides basic functions such as sign-up, sign-in, multi-factor authentication (MFA), and password reset.
- Also functions as a hub for integrating authentication with third-party identity providers (IdPs).
- Customizable, allowing creation of a branded appearance using logos and CSS.
- Handles routing of authentication requests, issuing and managing JSON Web Tokens (JWTs), and providing user attribute information.
For example, you can access the Hosted UI with a URL like this:
https://<your user pool domain>/authorize?client_id=<your app client ID>&response_type=<code/token>&scope=<scopes to request>&redirect_uri=<your callback URL>With the features of the Hosted UI, developers can easily implement the authentication process, providing a user-friendly authentication experience for users.
By using the Hosted UI of Amazon Cognito User Pools, developers can easily implement a secure and standardized authentication process without having to build complex authentication systems from scratch.
Types of Lambda Triggers
In Amazon Cognito User Pools, you can use Lambda triggers to execute custom logic at various stages of the user authentication process, allowing you to customize the authentication flow.The main processes that can be executed with Lambda triggers include the following:
- Sign-up Related
Pre sign-up: A trigger to perform custom validation or other pre-processing before sign-up. It can also approve or reject user registration.
Post confirmation: Processing that occurs after sign-up confirmation (after email or SMS verification) is completed, allowing for sending custom messages or recording logs. - Authentication Related
Pre authentication: A trigger to perform custom validation before authentication. For example, it can reject login for users meeting specific conditions.
Post authentication: A trigger to perform processes such as log recording or collection of analytics data after successful user authentication. - Custom Authentication Challenge Related
Define auth challenge: Determines the next challenge (authentication step) during the authentication process.
Create auth challenge: Creates a new authentication challenge.
Verify auth challenge response: Verifies the response from the user and determines the success or failure of authentication. - Token Generation Related
Pre token generation: A trigger to modify token claims or add new claims before ID tokens or access tokens are generated. - User Migration Related
Migrate user: A trigger to assist in migrating user information from an existing user directory to Amazon Cognito User Pool. It migrates information from the old system when a user signs in for the first time. - Message Customization Related
Custom message: A trigger to customize the content of messages sent via email or SMS. Language localization is also possible. - Custom Sender Related
Custom email sender: A trigger to customize and send emails using a third-party provider.
Custom SMS sender: A trigger to customize and send SMS messages using a third-party provider.
Amazon Pinpoint Analytics
Amazon Pinpoint is a multi-channel marketing platform that helps improve user engagement and conduct targeted campaigns.Amazon Pinpoint campaigns provide the ability to deliver specific messages or promotions to user segments.
Amazon Cognito User Pools integrates with Amazon Pinpoint, providing analytics capabilities for user pools and enhancing user data for Amazon Pinpoint campaigns.
This integration enables the following:
- Tracking of user pool sign-ups, sign-ins, authentication failures, daily active users (DAU), monthly active users (MAU), etc.
- Data analysis based on attributes such as device platform, device locale, app version, etc.
- Setting custom attributes and using them for user segmentation
- Sending targeted push notifications
There are limitations to the regional availability of Amazon Cognito and Amazon Pinpoint, and in some regions, Amazon Pinpoint projects need to be created in the same region or in us-east-1 (N. Virginia).
You can use the Amazon Cognito console, AWS CLI, or AWS API to specify analytics settings.
After configuration, you can pass metadata to Amazon Pinpoint by including the AnalyticsMetadata parameter in your application.
In this way, the integration of Amazon Cognito User Pools and Amazon Pinpoint enables improved mobile app user engagement and more effective targeting and analytics.
User Management
Using Amazon Cognito User Pools, you can create, confirm, and manage user accounts after creating a user pool.By utilizing user pool groups, you can map IAM roles to groups and manage users and their access to resources.
Also, it's possible to import users into the user pool using the Migrate user Lambda trigger.
This method enables seamless migration of users from an existing user directory to the user pool when users sign in for the first time.
After creating a user pool, you can efficiently manage users using the following features:
- Group Management
You can create groups within the user pool and manage user access permissions by mapping IAM roles. - User Migration
Using the Migrate user Lambda trigger, seamless migration from existing user directories to the user pool is possible. Users are automatically migrated when they sign in for the first time. - Policy Settings
You can set policies related to user creation to enhance security. - Account Management
As an administrator, you can create user accounts or search and manage existing accounts. - Account Recovery
Account recovery features are provided for cases such as when users forget their passwords. - Attribute Management
You can flexibly set attributes of the user pool to manage necessary information. - Password Requirements
You can add password requirements for the user pool to enhance security.
Accessing AWS Resources After Successful Authentication
As mentioned earlier, using Amazon Cognito User Pools, users can authenticate directly using the user pool or via third-party identity providers (IdPs).After successful authentication, the application receives user pool tokens from Amazon Cognito.
These tokens can be used for various operations such as:
- Obtaining AWS credentials to access resources of AWS services (like DynamoDB or S3)
- Providing temporary and revocable proof of authentication
- Populating identity data into user profiles within the application
- Authorizing profile changes for signed-in users within the user pool directory
- Authorizing requests for user information using access tokens
- Authorizing requests to external APIs using access tokens
- Authorizing access to application assets on the client or server using Amazon Verified Permissions
Available Security Features
Amazon Cognito User Pools provides various security features to protect user identities.The main security features provided by Amazon Cognito User Pools include the following:
- Multi-Factor Authentication (MFA)
You can add a second authentication factor in addition to username and password.
SMS text messages or time-based one-time passwords (TOTP) are available. - Adaptive Authentication
Adaptive Authentication is a security feature that analyzes user behavior patterns and risk factors to dynamically adjust the appropriate authentication level based on the situation.
It uses a risk-based model to predict whether additional authentication factors are needed.
This is provided as part of "Amazon Cognito Advanced Security," which requires additional fees. - Protection Against Compromised Credentials
It checks against a database of known leaked passwords to prevent users from using vulnerable passwords.
This is provided as part of "Amazon Cognito Advanced Security," which requires additional fees. - Integration with AWS WAF Web ACL
You can associate an AWS WAF Web ACL with your user pool. - Case Sensitivity in User Pools
You can manage the handling of case sensitivity for usernames and other attributes. - User Pool Deletion Protection
It prevents unintended deletion of user pools. - Managing User Existence Error Responses
You can customize error responses related to user existence.
Amazon Cognito Identity Pools
Overview of Amazon Cognito Identity Pools Features
Amazon Cognito Identity Pools is a service that grants temporary access rights to AWS resources for authenticated and unauthenticated users.Identity Pools issue AWS credentials not only to authenticated users but also to anonymous users, allowing applications to provide appropriate levels of resource access.
One of the notable features of Identity Pools is the ability to smoothly transition unauthenticated users to authenticated users, allowing users to start with limited guest access and then gain broader access rights after going through the authentication process.
This flexibility enables applications to simultaneously achieve new user acquisition and improved engagement.
Furthermore, Identity Pools integrates with various authentication providers.
It supports user pools, SAML 2.0 services, OIDC providers, social ID providers (such as Amazon, Facebook, Google, Apple, Twitter), and also allows custom authentication schemes.
This allows developers to choose the authentication method that best suits their needs.
An important characteristic of Identity Pools is the ability to combine role-based and attribute-based access control.
Role-based access control selects appropriate IAM roles based on user claims or attributes and applies finely tuned IAM policies to each role. Attribute-based access control extracts attributes from user claims and maps them to principal tags for temporary sessions, allowing for more precise control of resource access.
After configuring the Amazon Cognito credentials provider and obtaining AWS credentials, developers can create AWS service clients using these credentials, allowing applications to securely interact with various AWS services such as Amazon S3, Amazon DynamoDB, Amazon Pinpoint, and Amazon CloudWatch.
This feature allows developers to maximize the use of AWS's rich service ecosystem and build scalable and robust applications.
Overall, Amazon Cognito Identity Pools provides a comprehensive and flexible authentication and authorization solution from user authentication to AWS resource access management, allowing developers to achieve a seamless user experience without compromising security.
Role-Based Access Control (RBAC)
Amazon Cognito Identity Pools assigns temporary credentials with limited permissions to access AWS resources for authenticated users.The permissions for each user are controlled by IAM roles you create.
You can define rules to select which role to apply to each user based on claims in the user's ID token.
It's also possible to define a default role for authenticated users. For unauthenticated guest users, you can define a separate IAM role with limited permissions.
When creating roles for role mapping, it's important to add appropriate trust policies to each role.
This ensures that the role can only be assumed by Amazon Cognito for authenticated users within the Identity Pool.
There are mainly two ways to assign roles to users:
- Assigning Roles Using Tokens
For users logged in through a user pool, you can assign roles using specific claims in the ID token (cognito:preferred_role, cognito:roles). - Assigning Roles Through Rule-Based Mapping
You can set up rules to map claims from ID provider tokens to IAM roles. Each rule specifies a token claim, match type, value, and IAM role.
As a security best practice, it's important to map only claims that end users cannot directly configure to high-privilege roles.
You can also specify default behavior for cases where an appropriate role cannot be determined.
Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) in Amazon Cognito Identity Pools is a feature that controls access to AWS resources based on user attributes.Using this feature, you can map user attributes obtained from social or enterprise authentication providers to tags that can be referenced in IAM policies.
The main characteristics and benefits of ABAC are as follows:
- Efficient Permission Management
By using user attributes, you can create a single basic permission policy instead of creating multiple policies. - Policy Flexibility
There's no need to update policies when adding or removing resources or users. Policies only allow access to users with matching user attributes. - Attribute Mapping
You can choose default mappings or create custom mappings to set attributes referenced in IAM permission policies. - Conditional Access
You can conditionally allow or deny access to specific resources based on the user's attribute values.
It's also recommended to define default behavior for cases where attribute values are unknown or non-existent, and to control access following the principle of least privilege.
The trust policy of IAM roles needs to be properly configured to apply principal tags to user sessions.
Furthermore, it's important to use combinations of attributes to achieve more granular access control and to regularly review the relationship between attributes and policies to ensure that unnecessary permissions are not granted.
These practices allow for safer and more effective implementation of attribute-based access control.
Obtaining Credentials to Access AWS Resources
Using Amazon Cognito Identity Pools, you can provide your application with temporary credentials that have limited permissions to access AWS resources.There are important points in the process of obtaining credentials:
- Authenticated and Unauthenticated Identities
Unauthenticated users: Suitable for guest users who can access the app without identity verification.
Authenticated users: Login through third-party ID providers or user pools and have their identity verified. - Amazon Cognito Identities
The identity itself is not a credential.
It is exchanged for credentials through AWS Security Token Service (STS) web ID federation support. - Recommended Method for Obtaining Credentials
It is recommended to obtain AWS credentials from AWS.CognitoIdentityCredentials, which is the Amazon Cognito Identity Pools credentials object.
The identity within the credentials object is exchanged for credentials via AWS STS. - Utilizing integration with SDKs and AWS Amplify
AWS SDKs have built-in mechanisms (credential provider chain) to automatically discover and use credentials. Web ID credential providers (including Identity Pools) are part of this chain. This means that when using SDKs, you can easily utilize credentials from Identity Pools without additional configuration.
Additionally, AWS Amplify has built-in Identity Pool integration functionality, which can significantly simplify the implementation of authentication and user management, enabling reduced development time and more robust security implementation. - Resources for Various SDKs
Methods for obtaining and configuring credentials using Identity Pools are provided in SDKs for various programming languages and platforms, including Android, iOS, JavaScript, .NET, Go, Java, PHP, Python, and Rust.
Developer-Authenticated Identities
Developer-Authenticated Identities is one of the authentication methods provided by Amazon Cognito Identity Pools. This feature allows developers to register and authenticate users using their existing authentication processes while utilizing Amazon Cognito Identity Pools for user data synchronization and access to AWS resources.However, it is important to note that this feature is designed to be used in conjunction with Amazon Cognito Identity Pools and does not support Amazon Cognito User Pools.
The main characteristics of Developer-Authenticated Identities include:
- Custom Authentication
Developers can use their own authentication systems. - Backend Integration
Coordination between user devices, developer's backend, and Amazon Cognito Identity Pools. - Flexibility
Can be used in combination with Web ID Federation (Facebook, Google, Amazon, Apple, etc.), but may increase implementation complexity. - Security
Uses the GetOpenIdTokenForDeveloperIdentity API on the backend server for authentication with administrator credentials. Direct calls from the client-side are not recommended. - Implementation
As of the time of writing this article, implementation methods are provided in SDKs for Android, iOS, JavaScript, Unity, and Xamarin. - ID Pool Association
Uses developer provider names associated with ID pools. - Token Management
Requires a mechanism to obtain tokens on the backend and return them to the client. Also needs to consider token expiration management and renewal mechanisms. - Integration with Other Authentication Methods
Implementation methods are also provided for use with unauthenticated IDs and social ID providers.
- The application authenticates with its own backend.
- The backend calls Amazon Cognito Identity Pools'
GetOpenIdTokenForDeveloperIdentityAPI to obtain an ID token. - The backend returns the ID token to the application.
- The application uses this token to obtain AWS credentials.
To use Developer-Authenticated Identities, the following steps are necessary:
- Associate a developer provider name with an identity pool in the Amazon Cognito Identity Pools console.
- Set up appropriate IAM roles and policies for the identity pool.
- Implement a custom ID provider class on the application side.
- Call the
GetOpenIdTokenForDeveloperIdentityAPI on the backend to obtain and manage ID tokens.
External Identity Providers
Amazon Cognito Identity Pools supports integration with multiple external identity providers (IdPs), allowing users to authenticate in various ways.In Amazon Cognito Identity Pools, you can set authentication information from external IdPs using the logins property, which is an element used to configure credentials received from IdPs.
Furthermore, it's possible to associate one identity pool with multiple IdPs.
For example, by setting both Facebook and Google tokens in the logins property, you can associate one Amazon Cognito identity with multiple IdP logins.
As a result, users can authenticate with either account, and Amazon Cognito will return the same user identifier.
The main external IdPs supported by Amazon Cognito Identity Pools include:
- Login with Amazon
- Sign in with Apple
- OpenID Connect (OIDC) providers
- SAML providers
Security Best Practices
There are several important points in the best practices for enhancing the security of Amazon Cognito Identity Pools:- Principle of Least Privilege
Use IAM roles and policies to grant users only the minimum necessary permissions. - Utilization of Resource-Based Policies Use resource-based policies for fine-grained control over user access to resources.
- Use of Session Tags
Implement access control based on user characteristics by converting user claims to IAM session tags. - Restriction of Guest Access
Configure to generate only AWS credentials with limited scope for unauthenticated users. - Assignment of IAM Roles Based on User Characteristics
Assign appropriate IAM roles to authenticated users based on individual user claims. - Selection of Appropriate Authentication Providers
Choose and properly configure trusted authentication providers suitable for your use case. - Proper Implementation of Custom Authentication
When using developer-authenticated identities, implement and properly verify robust authentication mechanisms. - Regular Auditing and Monitoring
Regularly audit and monitor user activity using services such as Amazon CloudWatch.
Differences and Comparison between User Pools and Identity Pools
Amazon Cognito's User Pools and Identity Pools are two important components with different purposes and functions.User Pools primarily specialize in user authentication and management, functioning as a user directory for web and mobile applications.
It provides features such as local user creation, federation through third-party IdPs, multi-factor authentication (MFA), and custom authentication flows.
On the other hand, Identity Pools focus mainly on access control to AWS resources, issuing temporary AWS credentials to both authenticated and unauthenticated users.
Identity Pools enable fine-grained AWS resource access management through role-based access control and attribute-based access control.
By combining these two, secure and flexible user authentication and AWS resource access control can be achieved.
For example, it's possible to use tokens authenticated by User Pools in Identity Pools to obtain appropriate AWS credentials.
The following AWS documentation page contains a comparison table of the features of Amazon Cognito, User Pools, and Identity Pools.
Amazon Cognito user pools and identity pools comparison
Summarizing this content, the main differences between User Pools and Identity Pools include the following characteristics:
| Item | Amazon Cognito User Pools | Amazon Cognito Identity Pools |
|---|---|---|
| Authentication and Authorization |
Primarily focus on user authentication (OIDC IdP, SAML 2.0, OAuth 2.0, etc.) and API authorization. | Focus on issuing temporary AWS credentials. |
| Token Management | Issue and customize ID tokens and access tokens. | Manage temporary credentials in collaboration with AWS STS. |
| User Management | Provide functions for user registration, authentication, attribute management, MFA, security monitoring, etc. | Do not directly provide these functions. |
| Access Control | Can create a hierarchy of IAM role requests through group functionality. | Provide role-based and attribute-based access control, enabling fine-grained access management to AWS resources. |
| Unauthenticated Access | Do not have this functionality. | Can provide limited access even to unauthenticated users. |
| Customization | Customization features target authentication flows, user attributes, and ID tokens. | Customization features focus on access control. |
From these considerations, it would be best to choose Amazon Cognito Identity Pools if the main purpose is access control to AWS services, and Amazon Verified Permissions if complex application-specific authorization logic is required.
AWS AppSync and Amazon Cognito Sync
AWS AppSync and Amazon Cognito Sync are key AWS services responsible for data synchronization and management in cloud-based mobile and web application development.To conclude upfront, Amazon Cognito Sync is now deprecated, and the use of AWS AppSync is recommended.
Here, we'll explain the characteristics, differences, and reasons for the current recommendation of these services.
Main Differences
AWS AppSync is a fully managed service for managing application data using GraphQL. It can handle complex data structures and enable real-time data synchronization.Amazon Cognito Sync was a simple service for synchronizing user data across devices. It provided functionality to store and synchronize data in key-value pair format.
From different perspectives, there are the following differences:
| Item | AWS AppSync | Amazon Cognito Sync |
|---|---|---|
| Data Model | Uses GraphQL and can handle complex data structures and relationships. | Was limited to a simple key-value pair data model. |
| Scalability | Can handle large-scale applications and provides high scalability. | Was suitable for small to medium-scale applications. |
| Real-time Functionality | Supports real-time data updates using WebSockets. | Had limited real-time update functionality. |
| Integration | Can integrate with various AWS services (DynamoDB, Aurora, Elasticsearch, etc.). | Was primarily integrated closely with Cognito Identity Pools. |
| Developer Experience | Provides richer development tools and integration with AWS Amplify. | Was suitable for basic data synchronization tasks with a simple API. |
Current Recommendations and Reasons
AWS currently strongly recommends using AWS AppSync for new application development.On the other hand, Amazon Cognito Sync is deprecated and not recommended for new use.
The reasons behind this recommendation include:
- Superior flexibility and scalability of AWS AppSync
- Compatibility with modern application development needs
- Stronger security features and finer access control
- Increased demand for GraphQL adoption and efficient data retrieval
Therefore, for projects currently using Cognito Sync, it would be advisable to consider migrating to AppSync in the future.
Integration with AWS Services
Amazon Cognito provides a more powerful and flexible authentication and authorization solution by integrating with various AWS services.Here, we'll explain in detail three main integration methods.
These integrations allow developers to build the optimal authentication and authorization system for their application needs.
Integration with AWS Amplify
Amazon Cognito User Pools can be easily integrated into web and mobile apps through AWS Amplify.Amplify Auth primarily uses Amazon Cognito to build authentication functionality.
Developers can create and configure resources using the Amplify CLI, and implement features like sign-in and sign-up using Amplify libraries.
Furthermore, by utilizing Amplify's Authenticator component, you can easily build customizable authentication UIs.
This allows developers to maximize the features of User Pools while rapidly implementing a secure authentication system.
Integration with AWS SDKs
Both Amazon Cognito User Pools and Amazon Cognito Identity Pools can be integrated using AWS SDKs.Backend developers can interact directly with Amazon Cognito APIs using the SDK of their chosen language to build custom authentication microservices.
They can use User Pools APIs to control user management and authentication processes, and Identity Pools APIs to manage access permissions to AWS resources.
This allows developers to implement authentication and authorization systems with more granular control and flexibility.
Integration with Amazon Verified Permissions
Amazon Cognito User Pools can be integrated with Amazon Verified Permissions to achieve advanced authorization capabilities.Applications can pass access tokens or ID tokens issued by User Pools to Verified Permissions to obtain detailed authorization decisions.
Amazon Verified Permissions makes allow or deny decisions based on policies written in Cedar Policy Language, considering user attributes and request context.
Also, the policy store, a core feature of Amazon Verified Permissions, is a repository for centralized management of authorization policies.
When configuring a policy store, you select the token type to process (access token or ID token) and set up Amazon Cognito User Pools as the identity source.
Using a policy store allows you to hierarchically reference users, groups, actions, and resources within policies, enabling the definition of fine-grained authorization rules.
This integration allows you to combine the authentication capabilities of Amazon Cognito User Pools with the flexible authorization capabilities of Amazon Verified Permissions to achieve fine-grained access control.
Particularly, by integrating with Amazon API Gateway, it's possible to build a powerful authorization mechanism for RESTful APIs.
The authentication and authorization process and benefits of integrating Amazon Cognito User Pools with Amazon Verified Permissions can be summarized as follows:
Authentication Process with Amazon Cognito User Pools
- Users authenticate through Amazon Cognito User Pools.
- After successful authentication, User Pools issues an access token or ID token.
- The application passes this token to Verified Permissions to request an authorization decision.
Authorization Process with Amazon Verified Permissions
- Amazon Verified Permissions verifies the received token.
It checks the token's validity, issuer, expiration, etc.
It confirms that the user pool is a configured identity source for Amazon Verified Permissions. - It extracts information (claims) from the token and uses it as input for policy evaluation.
- It makes authorization decisions based on policies written in Cedar Policy Language.
User attributes (group membership, custom attributes, etc.)
Request context (resource identifiers, action types, etc.)
Other custom context information - It returns an Allow or Deny decision.
- Handling of token revocation and deleted users
Verified Permissions only verifies information available from the identity source and the user token's expiration.
It does not check the token's revocation status or whether the user has been deleted from the user pool.
Even if a token has been revoked or a user has been deleted from the user pool, the token is considered valid until it expires.
Benefits of Integrating Amazon Cognito User Pools with Amazon Verified Permissions
The benefits of integrating Amazon Cognito User Pools with Amazon Verified Permissions include:- Fine-grained Access Control
You can define detailed authorization rules based on user attributes, group membership, request context, etc. - Flexible Policy Management
You can express complex authorization logic using Cedar Policy Language. - Centralized Authorization
You can apply consistent authorization rules across the entire application. - Scalability
By using Amazon Verified Permissions' managed service, you can efficiently process authorization even in large-scale applications. - Combination of RBAC and ABAC
By using ID tokens, you can combine Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC).
This enables more granular authorization decisions based on user attributes and group memberships.
Process and Benefits of Using Amazon Cognito User Pools and Amazon Verified Permissions for Authentication and Authorization in Amazon API Gateway
As an example, we'll explain the process and benefits of using Amazon Cognito User Pools for authentication and Amazon Verified Permissions for authorization in Amazon API Gateway.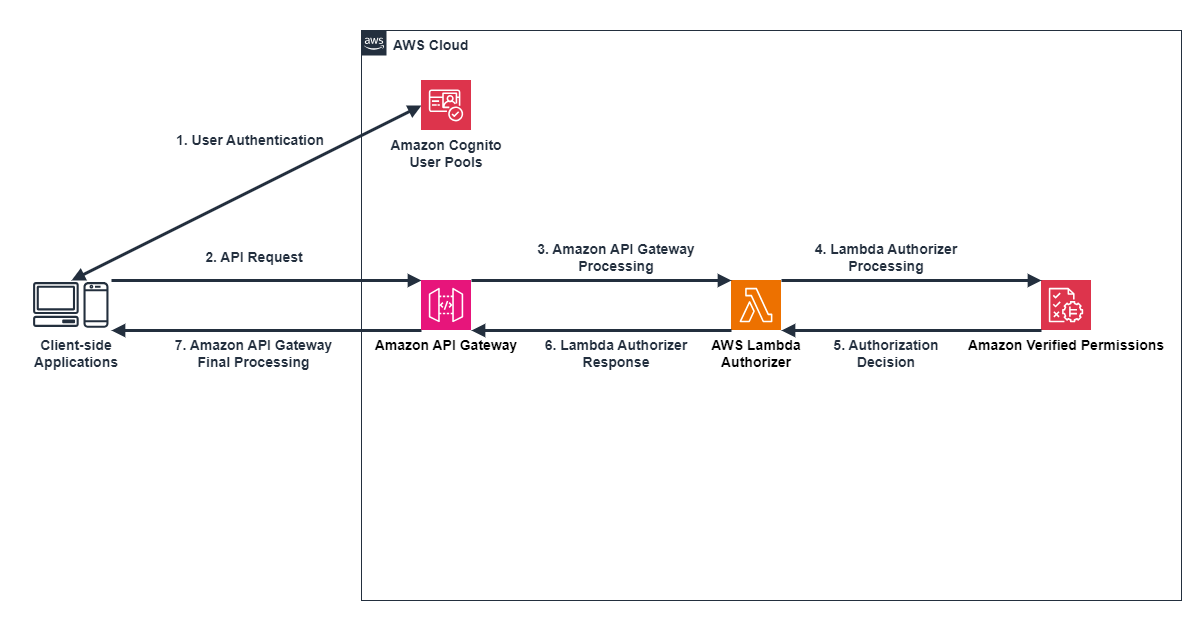
- Process when used for authentication and authorization in Amazon API Gateway
- User Authentication (Amazon Cognito User Pools)
Users authenticate through Amazon Cognito or other OIDC IdPs.
The IdP issues ID tokens and access tokens (JWT) containing user information. - API Request
The client includes the JWT in the Authorization header when sending a request to Amazon API Gateway. - Amazon API Gateway Processing
API Gateway uses the authorization decision cache if available.
If there's no cache or it's invalid, API Gateway invokes a Lambda authorizer. - Lambda Authorizer Processing
The AWS Lambda function sends an authorization request to Amazon Verified Permissions using the IsAuthorizedWithToken API.
It includes the user's token (principal), API method and path (action), and Application (resource). - Authorization Decision (Amazon Verified Permissions)
Amazon Verified Permissions verifies the token and makes authorization decisions based on policies written in Cedar Policy Language stored in the policy store.
It considers user attributes, request context, and other information to return an Allow or Deny decision. - Lambda Authorizer Response
The Lambda authorizer returns an Allow or Deny response to API Gateway based on the authorization result from Verified Permissions. - Amazon API Gateway Final Processing
API Gateway returns data or an ACCESS_DENIED response based on the Lambda authorizer's result.
- User Authentication (Amazon Cognito User Pools)
- Benefits when used for authentication and authorization in Amazon API Gateway
The benefits of using this for authentication and authorization in Amazon API Gateway include:
- Secure Authentication
You can leverage the robust authentication mechanism of Amazon Cognito User Pools.
You can utilize features such as multi-factor authentication and integration with social ID providers. - Fine-grained Authorization Control
You can define detailed authorization rules using Amazon Verified Permissions.
Authorization based on user attributes, group membership, request context, etc. is possible. - Flexible Policy Management
You can express complex authorization logic using Cedar Policy Language.
Central management of policies is possible, allowing consistent authorization rules to be applied. - Scalability and Performance
API Gateway, Cognito, and Verified Permissions are all managed services that provide high scalability.
Using Lambda authorizers allows customization of authentication and authorization logic. - Enhanced Security
Separating authentication and authorization allows for a more secure architecture.
Token-based authentication enables stateless and secure communication. - Improved Development Efficiency
Authentication and authorization logic can be separated from application code.
Using managed services allows developers to focus on essential business logic.
- Secure Authentication
Differences in Roles and Uses between Amazon Cognito Identity Pools and Amazon Verified Permissions
Both Amazon Cognito Identity Pools and Amazon Verified Permissions provide authorization functionality after authentication with Amazon Cognito User Pools.However, there are the following differences in their roles and uses:
| Item | Amazon Cognito Identity Pools | Amazon Verified Permissions |
|---|---|---|
| Main Role | Granting temporary access permissions to AWS services. | Fine-grained application-level authorization. |
| Characteristics |
|
|
| Usage Examples | When accessing S3 buckets directly from mobile apps, etc. | For permission management in applications with complex organizational structures, when dynamic access control is needed, etc. |
| Scope | Mainly focused on access to AWS services. | Emphasis on application-specific authorization. |
| Granularity | Relatively coarse-grained control based on IAM roles. | Allows for finer-grained control. |
| Control Flexibility | Control through IAM policies. | Can define more complex and dynamic authorization rules using Cedar language. |
From these considerations, it would be best to choose Amazon Cognito Identity Pools if the main purpose is access control to AWS services, and Amazon Verified Permissions if complex application-specific authorization logic is required.
References:
Tech Blog with curated related content
AWS Documentation(Amazon Cognito)
Summary
This time, I created a timeline of Amazon Cognito's history and reviewed the list of Amazon Cognito's features and their overview.Since its launch in 2014, Amazon Cognito has been continuously providing highly convenient security features for application developers, eliminating the complexities of user authentication and authorization.
User Pools simplify the sign-up and sign-in processes and offer a user-friendly authentication experience for end-users by providing various authentication options.
On the other hand, Identity Pools authorize secure access to AWS resources by providing temporary AWS credentials to both authenticated and unauthenticated users.
Moreover, over the past 10 years, Amazon Cognito has made many important updates, gradually expanding its features such as social login support, managed user directories, application data synchronization, and enhanced security. Particularly, recent updates, like the integration with Amazon Verified Permissions, tend to introduce features that further improve security and convenience.
The future direction of Amazon Cognito is expected to continue adding features that address the security and user management needs of applications.
I would like to continue monitoring the trends of what kind of features Amazon Cognito will provide in the future.
In addition, there is also a historical timeline of all AWS services including services other than Amazon Cognito, so please have a look if you are interested.
AWS History and Timeline - Almost All AWS Services List, Announcements, General Availability(GA)
Written by Hidekazu Konishi