Setting up DKIM, SPF, DMARC with Amazon SES and Amazon Route 53 - An Overview of DMARC Parameters and Configuration Examples
First Published:
Last Updated:
Additionally, if sending more than 5000 emails per day to Gmail accounts, setting up DMARC (Domain-based Message Authentication, Reporting, and Conformance) is also necessary.
Reference: Email sender guidelines - Google Workspace Admin Help
Due to these circumstances, there has been an increase in discussions about DKIM, SPF, and DMARC settings recently. Considering future email sending with new domains, I personally researched and compiled a memo on setting up DKIM, SPF, and DMARC with Amazon SES and Amazon Route 53.
Furthermore, I would like to include notes on record settings when using DNS services other than Amazon Route 53 and an overview and example settings of DMARC parameters.
*The source code and settings presented in this article and other articles by the author were created as part of independent research activities and are not guaranteed to work. Please use them at your own risk. Note that they may be modified without notice.
*For this article, AWS services were used on an AWS account registered personally.
Overview of DKIM, SPF, DMARC
Before diving into the specific settings for Amazon SES and Amazon Route 53, I'll explain the basics of DKIM, SPF, and DMARC.DKIM, SPF, and DMARC are three major technologies designed to improve email security, enhance the authentication process during email sending, and prevent fraudulent activities like phishing and spoofing.
These technologies complement each other, providing robust security against email-based attacks. Domain owners can prevent unauthorized email sending and increase sender reliability by properly setting up and managing these technologies.
Below is a brief explanation of each technology.
What is DKIM?
DKIM (DomainKeys Identified Mail) is a mechanism that allows email senders to prove to recipients that their email is legitimate.DKIM adds a digital signature to emails, which is verified using a public key associated with the sender's domain.
Recipients use the public key (published in DNS records) to verify the signature and ensure the email has not been tampered with.
This guarantees the authenticity and integrity of the email.
What is SPF?
SPF (Sender Policy Framework) is a technology for verifying the source of emails sent from a domain.Domain owners publish an SPF record in DNS, listing the IP addresses that are authorized to send emails from that domain.
Incoming mail servers refer to this record to check whether an email comes from an authorized IP address.
This helps prevent the transmission of spoofed emails.
What is DMARC?
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a policy that allows domain owners to specify how to handle emails based on the results of DKIM and SPF authentication.The DMARC policy is set in DNS records and specifies how to handle authentication failures (report only, quarantine, or reject).
It also sends authentication results and policy violation reports to the domain owner, making the email authentication process transparent and protecting the domain's reputation.
Setting up DKIM and SPF in Amazon SES
Now, let's discuss the specific settings for Amazon SES and Amazon Route 53.Setting up DKIM and SPF is straightforward with Amazon SES.
Additionally, if you use Amazon Route 53 as your domain's name server, it automatically sets up DNS records in the Hosted zone for you.
By default, Amazon SES sends messages using the
amazonses.com subdomain as the MAIL FROM domain.This default MAIL FROM domain matches the Amazon SES application sending the email, thus passing SPF authentication by default.
However, if you want to use a subdomain of your own domain as the MAIL FROM domain, you need to set up a "Custom MAIL FROM domain" in Amazon SES.
Furthermore, to comply with DMARC in Amazon SES, you need to implement either SPF compliance, DKIM compliance, or both.
To comply with DMARC via SPF in Amazon SES, you need to set up a "Custom MAIL FROM domain".
References:
Using a custom MAIL FROM domain - Amazon Simple Email Service
Complying with DMARC authentication protocol in Amazon SES - Amazon Simple Email Service
For this article, I will discuss setting up a "Custom MAIL FROM domain", including using a subdomain of my own domain instead of the default
amazonses.com domain.If using Amazon Route 53
If you are using Amazon Route 53 as your domain's name server and have created a Hosted zone, you can set up DKIM and SPF by following these steps:- Log in to the AWS Management Console.
- Navigate to Amazon SES > Verified identities > Create identity (Open the "Create identity | Amazon Simple Email Service | us-east-1" screen).
- Refer to the following example settings as you fill in the screen items, and click the "Create identity" button (adjust the settings as necessary for your requirements).
- Identity details settings
Identity type: Select "Domain".
Domain: Enter the domain you will use for email sending.
Use a custom MAIL FROM domain: Check the checkbox.
MAIL FROM domain: Enter the subdomain you will use for the Custom MAIL FROM domain.
Behavior on MX failure: Select "Use default MAIL FROM domain".
Publish DNS records to Route53: Check "Enabled". - Verifying your domain settings
Open the "Advanced DKIM settings" menu.
Identity type: Select "Easy DKIM".
DKIM signing key length: Select "RSA_2048_BIT".
Publish DNS records to Route53: Check "Enabled".
DKIM signatures: Check "Enabled".
- Identity details settings
An example of the "Create identity" screen settings in the Amazon SES console is shown below (this example sets the Domain to
ho2k.com and the MAIL FROM domain to email.ho2k.com).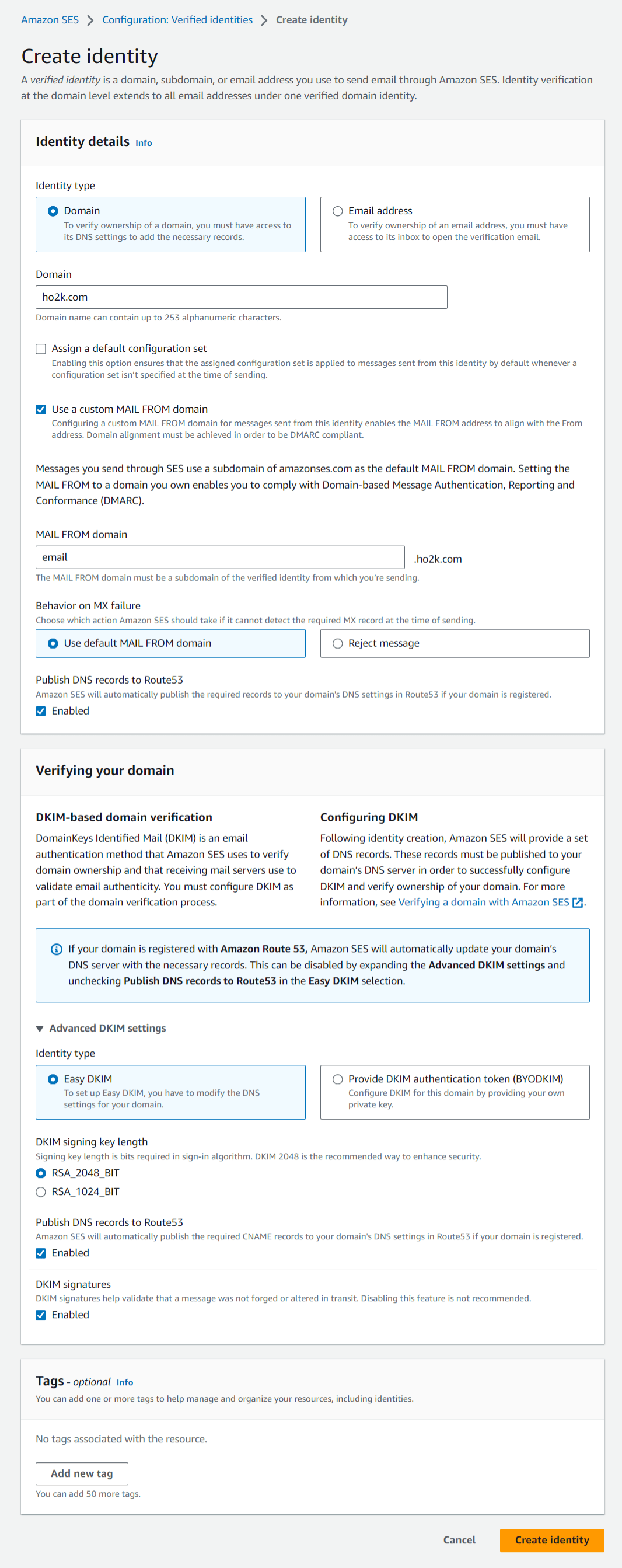
After executing "Create identity", the domain used for email sending is added to "Verified identities", and the DNS records required for DKIM and Custom MAIL FROM domain verification are automatically added to Amazon Route 53.
Here are examples of DNS records added to Amazon Route 53 for DKIM and Custom MAIL FROM domain verification (in this example, the Domain is set to
ho2k.com, and the MAIL FROM domain is set to email.ho2k.com).DKIM Verification DNS Records
| Type | Name | Value |
|---|---|---|
| CNAME | xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx._domainkey.ho2k.com |
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.dkim.amazonses.com |
| CNAME | yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy._domainkey.ho2k.com |
yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy.dkim.amazonses.com |
| CNAME | zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz._domainkey.ho2k.com |
zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz.dkim.amazonses.com |
However, this is normal behavior and part of the SES public key rotation process.
As new keys are generated and old keys are phased out, empty records indicate keys that are no longer used, a necessary process for maintaining security.
This phenomenon is not a configuration error but part of the automatic key update process.
Below is an example output when checking DKIM verification DNS records with the dig command.
[ho2k_com@ho2k-com ~]$ dig TXT xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx._domainkey.ho2k.com +short xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.dkim.amazonses.com. "p=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" "BBBBBBBBBBB BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB" [ho2k_com@ho2k-com ~]$ dig TXT yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy._domainkey.ho2k.com +short yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy.dkim.amazonses.com. "" [ho2k_com@ho2k-com ~]$ dig TXT zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz._domainkey.ho2k.com +short zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz.dkim.amazonses.com. ""
Reference: DKIM Troubleshooting Series: Your DKIM Status is Pending | AWS Messaging & Targeting Blog
Custom MAIL FROM domain Verification DNS Records
| Type | Name | Value |
|---|---|---|
| MX | email.ho2k.com |
10 feedback-smtp.us-east-1.amazonses.com |
| TXT | email.ho2k.com |
"v=spf1 include:amazonses.com ~all" |
"v=spf1 include:amazonses.com ~all", which corresponds to the SPF record.If not using Amazon Route 53 (using other DNS services)
If you are not using Amazon Route 53, such as when using other DNS services, execute "Create identity" without checking "Enabled" for "Publish DNS records to Route53".Then, navigate to the domain's screen in "Verified identities" and set the displayed DKIM and Custom MAIL FROM domain verification DNS records in your DNS service's zone.
When setting DKIM and Custom MAIL FROM domain verification DNS records in other DNS services, keep the following main points in mind:
- Enter CNAME and MX records with a
.(dot) at the end of the Value. - Enter TXT records with the Value enclosed in
"(double quotation marks) as is.
Setting up DMARC in Amazon SES
To set up DMARC in Amazon SES, add a DMARC record with your DMARC policy to your DNS service's zone.This is common whether you are using Amazon Route 53 or not.
Next, we'll explain the parameters in a DMARC record and provide an example of a DMARC record.
DMARC Record Parameters
The table below includes a brief explanation of each DMARC parameter and the value for each parameter.Use these parameters to set your DMARC policy in a DMARC record.
| Parameter | Overview |
|---|---|
| adkim | Alignment mode for DKIM identifiers (r = relaxed, partial match is acceptable; s = strict, exact match required) |
| aspf | Alignment mode for SPF identifiers (r = relaxed, partial match is acceptable; s = strict, exact match required) |
| fo | Options for failure reports (0 = report only if both authentication methods fail, 1 = report if either authentication fails, d = report only DKIM verification failure, s = report only SPF verification failure) |
| p | Desired action for mail receivers on authentication failure (none = no action, only report, quarantine = quarantine the mail (e.g., move to spam folder), reject = reject the email reception) |
| pct | Percentage of mail to which the policy applies (0-100, default is 100; apply policy at specified percentage) |
| rf | Format of failure reports (afrf = Authentication Failure Reporting Format, iodef = Incident Object Exchange Format) |
| ri | Interval for sending aggregate reports (specified in seconds, default is 86400 seconds = 24 hours; controls frequency of reports) |
| rua | Destination for aggregate reports (specified by URI; e.g., mailto:example@example.com) |
| ruf | Destination for failure reports (specified by URI; e.g., mailto:fail@example.com) |
| sp | Policy for subdomains (none, quarantine, reject; specify if different from main domain policy) |
| v | Version number (currently DMARC1 only; specifies version of DMARC) |
About DMARC Alignment
Alignment in DMARC ensures that an email is indeed from a legitimate sender by strictly evaluating the match of domain names in the email authentication process.Through alignment, DMARC rigorously assesses both DKIM and SPF authentication results to verify domain name matches.
Next, I will describe the concept of alignment and how alignment settings affect DMARC policy.
What is Alignment?
Alignment evaluates how the domain in the email'sFrom header matches the domain used in the DKIM signature's d= tag or the Return-Path domain used for SPF.This evaluation determines whether the email comes from a legitimate source.
DMARC includes alignment for both DKIM (adkim) and SPF (aspf), with two modes of alignment:
relaxed and strict.Alignment settings adjust the effect of DMARC policy, where
relaxed mode allows for more flexible authentication, reducing the risk of legitimate emails being falsely rejected, while strict mode provides stricter authentication, enhancing security but increasing the risk of misconfiguration leading to the acceptance of fraudulent emails.Domain owners must choose the appropriate alignment mode based on their security needs and risk tolerance, as accurate alignment settings are crucial for preventing unauthorized email sending and ensuring the delivery of legitimate emails.
DKIM Alignment (adkim)
- Relaxed Mode (
r): In this mode, a partial match between the sending domain and the DKIM signature's domain is acceptable. Specifically, differences in subdomains are allowed as long as the main domain matches. - Strict Mode (
s): This mode requires an exact match of the entire domain name, including subdomains.
SPF Alignment (aspf)
- Relaxed Mode (
r): For SPF,relaxedmode also allows a partial match of the main domain, accepting partial matches. - Strict Mode (
s): This mode requires the email'sReturn-Pathdomain to exactly match the domain in theFromheader.
Example of a DMARC Record
Using the DMARC record parameters mentioned above, an example of a DMARC record would look like this:| Type | Name | Value |
|---|---|---|
| TXT | _dmarc.ho2k.com |
"v=DMARC1; p=none; rua=mailto:dmarc@ho2k.com; ruf=mailto:dmarcfail@ho2k.com; sp=none; pct=100" |
v=DMARC1: This indicates the version of DMARC being used, currentlyDMARC1. A DMARC record must start with this field, declaring it as a DMARC policy statement.p=none: This specifies the action domain owners wish to be taken for emails that do not comply with DMARC.nonemeans no specific action will be taken for non-compliant emails, but reports will be received. This mode is primarily used for monitoring and troubleshooting policies, not actually rejecting or quarantining emails, often referred to as "monitor mode".rua=mailto:dmarc@ho2k.com: This specifies the email address to receive aggregated DMARC reports. Aggregate reports provide an overview of all emails sent from the domain, compliant or not, usually sent once a day.ruf=mailto:dmarcfail@ho2k.com: This specifies the email address to receive failure reports (forensic reports) for individual non-compliant emails. These reports provide detailed information about policy violations, aiding in diagnosis.sp=none: This specifies the policy applied to subdomains, withnonemeaning that the same DMARC policy as the main domain applies to subdomains, taking no specific action for non-compliant emails.pct=100: This parameter specifies the percentage of emails to which the policy applies.100means that all emails sent from the domain (100%) are subject to this DMARC policy.
This allows domain owners to identify and resolve authentication issues.
Additionally, it can be used as a preparatory step before switching to stricter policies such as
quarantine or reject in the future.However, this is just an example, so when setting up a DMARC record, please configure DMARC parameters according to your requirements.
If specifying
rua and ruf, be aware that reports might be sent to the email addresses, so you need to have a mail server capable of receiving emails or set up "Email receiving" in Amazon SES to receive emails.For setting up "Email receiving" in Amazon SES, please refer to the following AWS document.
Email receiving with Amazon SES - Amazon Simple Email Service
Verifying DKIM, SPF, DMARC in a Gmail Account
To verify whether emails sent from Amazon SES to a Gmail account pass DKIM, SPF, and DMARC, send a test email from Amazon SES.To send a test email from Amazon SES, navigate from "Verified identities" to the domain's screen, click the "Send test email" button on the top right to go to the "Send test email" screen, and send a test email to your Gmail account.
For how to use the "Send test email" screen, please refer to the following AWS document.
Sending test emails in Amazon SES with the simulator - Amazon Simple Email Service
Open the received test email in your Gmail account, select "Show original" from the three dots menu on the top right, and you can confirm that DKIM, SPF, and DMARC all pass as shown in the following example of the "Original Message" screen (this example is for sending an email with the domain
ho2k.com).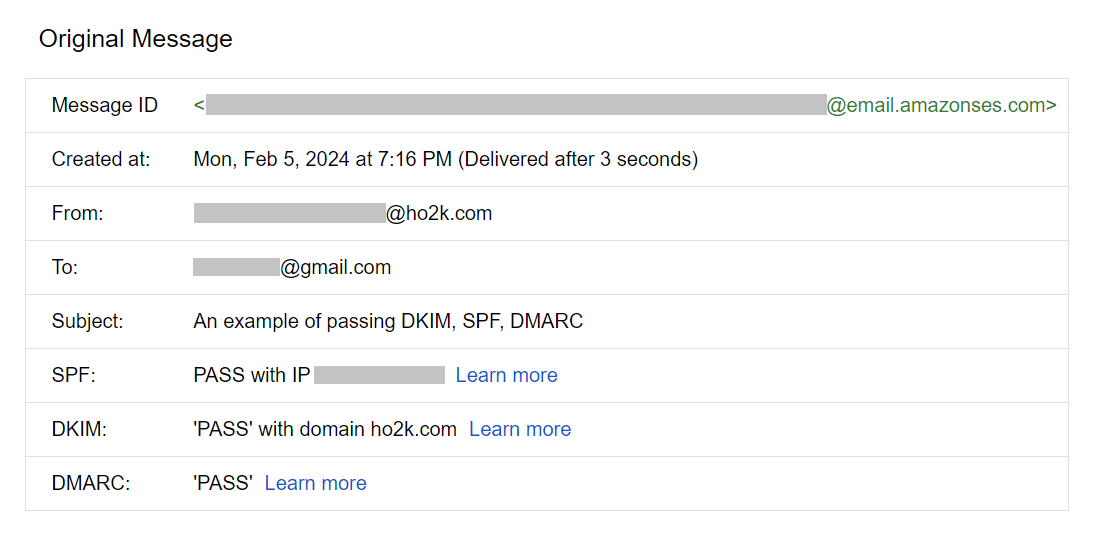
References:
Tech Blog with curated related content
Email sender guidelines - Google Workspace Admin Help
Define your DMARC record - Google Workspace Admin Help
What is Amazon SES? - Amazon Simple Email Service
Summary
This article explains how to set up DKIM, SPF, and DMARC using Amazon SES and Amazon Route 53, along with important considerations when using DNS services other than Amazon Route 53.I also covered how to set a DMARC policy in a DMARC record, including parameters and an example.
Furthermore, I confirmed that emails sent from Amazon SES to a Gmail account passed DKIM, SPF, and DMARC authentication.
Using Amazon SES and Amazon Route 53 together makes it easier to manage DKIM, SPF, and DMARC settings in email sending services.
When Amazon SES and Amazon Route 53 can be leveraged, it's beneficial to maximize their advantages while staying updated with new developments.
Written by Hidekazu Konishi